"I'll just make a few quick changes to the ecosystem this week. Seems like a nice way to come back from my time off over Thanksgiving."
—Me, a more naive person two weeks ago than I am today.
What started as "a few quick changes" turned into a long and intellectually grueling two-week project.
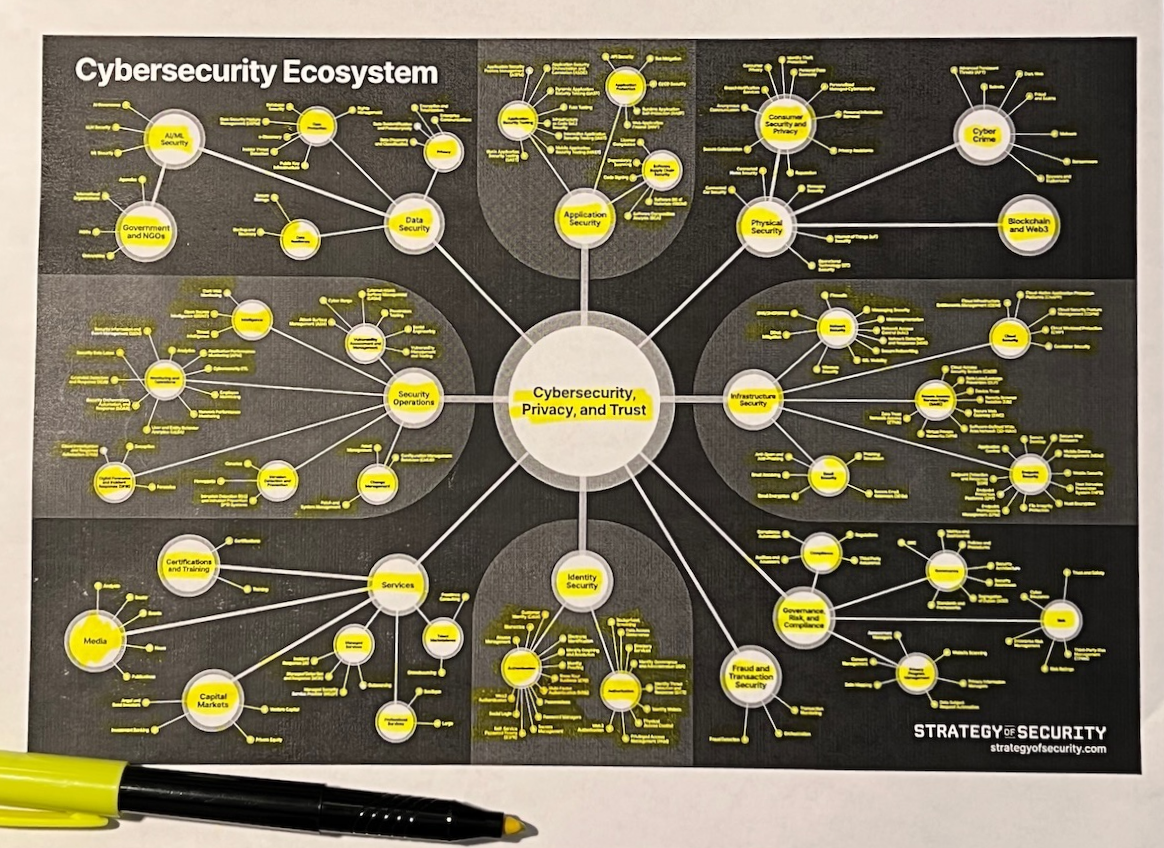
The result was the biggest update I've made to Strategy of Security's cybersecurity ecosystem mapping since I first published it over two years ago. A lot has changed since then, including both the industry and my own understanding of it.
This isn't your normal Strategy of Security article. It's a few things: an announcement about the updates, some observations and insights I had along the way, and an audible sigh of relief for finally being done (for now...).
One thing I want to be clear about: this is not an attempt to simplify anything about the industry — it's the opposite. My goal is to define the most comprehensive and accurate taxonomy for the business of cybersecurity as I can. The topic is complex, nuanced, and ...well, so is this mapping.
I think about the famous line from George Box a lot: "all models are wrong, some are useful." It's definitely true of this project. Only now, it's a little less wrong and a little more useful.
Let's talk about a few things I realized from obsessing about the cybersecurity ecosystem every waking hour for two straight weeks.
The big estates are clear, and more are on the way
I've been on a kick about cybersecurity estates for most of the past year. My irrational enthusiasm about this idea has now fully made its way into this cybersecurity ecosystem mapping.
The graphic is now reorganized around the four largest estates — Application Security, Identity Security, Infrastructure Security, and Security Operations. I felt good about this idea when I wrote my thoughts on cybersecurity estates a few weeks ago. I feel even better about it now.
Cybersecurity's four largest estates are clear. They're supported by both intuition and data. Most of cybersecurity's public companies and invested capital live there. Estates are also the epicenter of strategic activity in cybersecurity, and sometimes all of tech.
My mind really got bent when I realized how many other sectors are so obviously on their way to becoming massive estates. They may not have clear winners or public companies yet, but you can feel the momentum and see multiple companies on a sky high trajectory.
Let's take Governance, Risk, and Compliance as an example. It's easy to sleep on this sector because it has no rizz. But a savvy observer sees the appeal: new SEC cybersecurity disclosure rules, emerging cybersecurity and privacy regulations in the U.S. and Europe, CISO fraud charges, and more are making this market...surprisingly popular.
You could also make a case that Consumer Security and Privacy, Fraud and Transaction Security, Data Security, and Services are already estates. Each has one or more public companies, plus multiple startups valued at $1 billion or more. More importantly, these companies need to exist — they're solving some of the gnarliest problems in our industry.
The cybersecurity ecosystem is crowded, but it's still big enough for more estates. A rare few companies are even starting to transcend estates. Let's talk about that next.
A few companies are transcending estates
Here's a question I didn't consider until this year: "What happens when a company has billions of dollars in revenue and operates across multiple estates?"
We're at a point now where this question isn't just a thought experiment — it's a reality. Several companies have industry-leading products in multiple estates.
Big tech aggregators like Microsoft, Cisco, and Alphabet (Google Cloud) all have multi-billion-dollar cybersecurity businesses. They make high-stakes strategic maneuvers, like buying companies for $28 billion. They're so big that even the biggest pure cybersecurity companies are doing $1 billion in revenue through them.
Pure cybersecurity companies like CrowdStrike and Palo Alto Networks are combining multiple categories into platforms. They're generating billions in revenue and growing revenue at 20% or more. And investors have big expectations for the future — the two companies are currently valued at a combined total of $151 billion.
We're in an era of cybersecurity juggernauts. Once you understand how today's juggernauts are shaping the ecosystem, you start to notice the juggernauts of tomorrow.
The juggernauts of tomorrow are converging smaller markets
After the concepts of aggregation and platformization click in your mind, you can see little pockets of convergence happening everywhere. The juggernauts of tomorrow are building mini-platforms, combining old and new markets to own a valuable slice of the industry.
Application Security Posture Management (ASPM) is a good example. Companies are converging several types of application security testing tools (and adding a real-time component) to create end-to-end Application Security Testing platforms.
We're at a point where convergence is happening on top of convergence. Cloud-Native Application Protection Platforms (CNAPP) are really going for it — they're combining the core parts of the Cloud Security market (CSPM, CIEM, CWP, etc.) and taking over AppSec, too.
Companies who succeed at converging smaller markets to create bigger ones are going to enter the juggernaut territory of CrowdStrike and Palo Alto Networks.
This brings us to the most important lesson of all...
You never have the cybersecurity ecosystem totally figured out
I'll admit it: I was feeling prettyyyyyy good about my understanding of the ecosystem when I started these updates two weeks ago.
Now, in the last few words of a long and humbling process, I'm viscerally aware that none of us have the cybersecurity ecosystem totally figured out.
I say this with complete gratitude and excitement about the future. It's energizing to be part of an industry so dynamic. I like not having it all figured out.
Fully understanding cybersecurity is an ideal, not a realistic achievement. But it's the only motivation you need to keep trying.
Thank you to Nipun Gupta for helping me sort out the current application security landscape.

