Industry consolidation and Aggregation Theory are invisible forces that redefine entire markets. To the untrained eye, the changes they cause look shocking and unexpected. They're not (quite) as shocking if you know what to look for.
Most of the discussion we see about aggregation is at the tech industry level. Stratechery alone has written over a dozen articles about aggregators like Facebook, Google, Netflix, Airbnb, and others.
Within cybersecurity, we barely see any discussion at all about Aggregation Theory and how it's impacting the companies within our ecosystem. We do talk about consolidation a bit more, especially in the context of traditional mergers and acquisitions. However, the impact of both topics cannot be overstated. At a macro level, these are essential business concepts to understand.
Concepts like these are squarely at the intersection of strategy and cybersecurity — so, right up my alley. The goal of this article is to interpret and relate these concepts directly to cybersecurity. They need to be more approachable and relatable before they can be widely understood.
This article is an introduction to an ongoing series of discussions about the strategic impact of consolidation and aggregation in cybersecurity. It could have easily been a 10,000 word piece. There's a lot to say and many interesting examples to explore.
Today, we're going to cover:
-
The relationship and differences between consolidation and aggregation
-
How industry consolidation works, including examples in cybersecurity
-
What Aggregation Theory is and how it's likely to impact the cybersecurity ecosystem
These are intellectually complex (and sometimes mind-bending) topics. I've done my best to balance providing background with cybersecurity-specific examples and discussion. Don't worry if this article takes you some time to read and digest — it took me a long time to write it, too. Let's get to it.
The Relationship Between Consolidation and Aggregation
At an industry level, consolidation and aggregation are two of the major strategic forces that determine how companies and market segments shift over time — whether that's combining, separating, or creating something entirely new.
One of the primary concepts in business strategy (and industry analysis, specifically) is the idea of industry lifecycle stages. Consolidation tends to occur as industries reach later lifecycle stages, so it's worth digging into this idea a bit more.
Every industry follows a pattern, regardless of domain or size. The lifecycle of an industry is sort of like gravity in business — something we should basically accept as science and never attempt to defy. If you find someone (or yourself) thinking that an industry doesn't fit this pattern, you need to be suspicious.
The whole concept of an industry lifecycle can be summarized in a single chart:

Any industry segment (or company within a segment) can be plotted along the curve. Based on where the plot is, we can expect a generally predictable set of events to happen. The model isn't exact — it's just not reasonable to expect a model to predict the future — but it's incredibly powerful for pointing us in the right direction to connect the dots ourselves.
Specific types of events happen at each lifecycle stage:
-
Embryonic: Every new industry starts with a small, fragmented set of companies that are high risk bet. Basically everything is uncertain, including the viability of companies in the new industry. For example, do you know if companies building identity wallets are going to work out? I sure don't.
-
Growth: As the early-stage companies gain traction and grow, demand and profits start to increase. This is where Product-Market Fit (PMF) happens in tech. The pace is fast, but it's a good place to be as an industry. Companies like Snyk are at this stage right now.
-
Shake out: Competition increases because the idea has been validated by early stage companies. Growth slows, and competition becomes intense.
-
Mature: Once industries mature, achieving even single digit year-over-year growth is challenging. However, established companies in successful industries earn repeatable revenue and profits. Consolidation occurs between competitors because joining forces is one of the few ways left to gain market share. It's happening with legacy enterprise security companies like McAfee, Symantec, etc.
-
Decline: All industries will eventually decline, often after seemingly unrelated technology shifts change the existing business model completely. Industry decline is the territory of newspapers, Kodak, and Blockbuster. We actually haven't experienced it much in cybersecurity yet.
Cybersecurity is no exception — every part of the ecosystem follows industry lifecycle stages just like the rest of the business world.
This is where the idea of cybersecurity being an ecosystem matters. You can analyze cybersecurity as a whole using the industry lifecycle model, but it's a lot more useful to look at specific market segments within cybersecurity instead.
As the quick examples above illustrated, different segments can be at different points of the industry lifecycle, even if they're both part of the cybersecurity ecosystem. We'll discuss some more examples later.
Aggregation Theory is more complex to understand. The theory was developed by Stratechery author Ben Thompson in 2015 and builds on a few earlier concepts from Clayton Christensen and others. It's now one of the foundational ideas in modern tech strategy.
Here's a concise definition straight from Ben Thompson:
Aggregation Theory describes how platforms (i.e. aggregators) come to dominate the industries in which they compete in a systematic and predictable way.
The fundamental shift described by Aggregation Theory is a change in the nature of distribution:
...value has shifted away from companies that control the distribution of scarce resources to those that control demand for abundant ones...
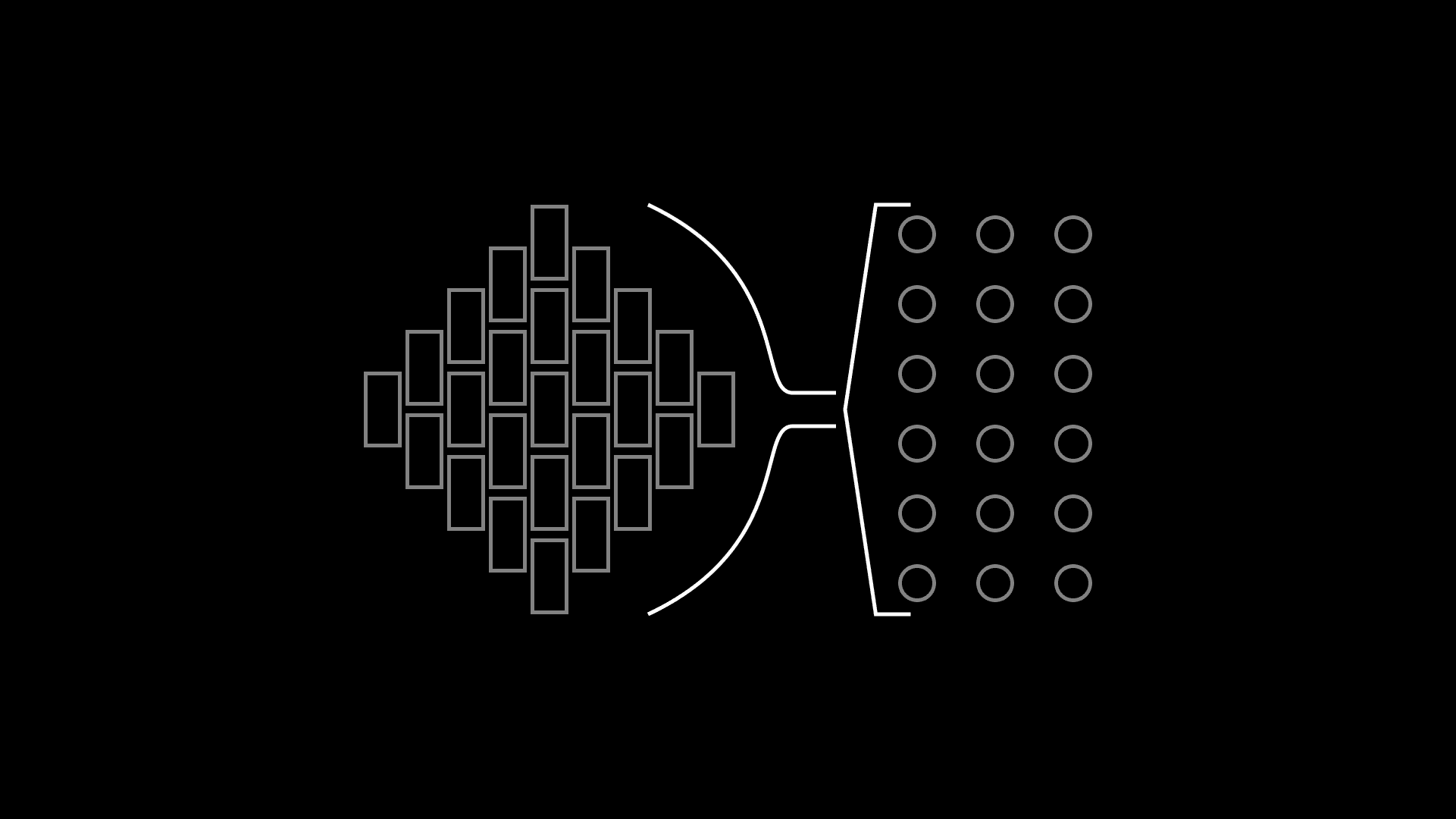
In the pre-internet era, distribution looked like this:

With aggregation, the new paradigm looks like this:

The evolution in distribution from control of scarce resources to demand for abundant ones explains many examples of innovation we see today — everything from newspapers and media to hotels and transportation. There is plenty of analysis about aggregation in tech (here's Stratechery on Airbnb, for example). Nobody talks about Aggregation Theory and cybersecurity, though. It's time to change that, and we'll start later in this article.
Like consolidation, aggregation is a trait that can happen to some companies and industries as they move along the industry lifecyle. It doesn't always happen — in fact, very few companies are true aggregators. However, if a company becomes an aggregator, it's essentially an unstoppable force.
Before we move into specific discussions about consolidation and aggregation, we need to finish by summarizing the relationship between the two concepts. The important difference is this: you can have consolidation without aggregation, and aggregation without consolidation.
Consolidation happens much more frequently than aggregation, and it occurs in more straightforward ways — mostly a flurry of mergers and acquisitions. Aggregation rarely happens, but it has the potential to change everything when it does.
Now that we have the definitions and nuances about consolidation and aggregation defined, it's time to talk about the impact of each in cybersecurity.
Consolidation Is Happening in Cybersecurity...
I have discussed the topic of consolidation in a few previous articles, mostly focused on specific companies (like CrowdStrike) or industry segments (like professional services). However, I haven't taken a step back yet to discuss why all of this consolidation is happening. That's the goal for this section.
Ironically, Aggregation Theory is a great way to explain the macro-level drivers behind consolidation. When a company is not an aggregator (remember, most aren't!), their growth slows as they move further along the maturity curve of the traditional industry lifecycle. From Stratechery:
...non-aggregator and non-platform companies face increasing customer acquisition costs as their user base grows. That is because initial customers are often a perfect product-market fit; however, as that fit decreases, the surplus value from the product decreases as well and quickly turns negative.
Inevitably, this is exactly what happens (or will happen) to most market segments within cybersecurity: growth eventually slows as a companies in the segment start reaching the top end of their Target Addressable Market (TAM). When growth slows, guess what happens? Yep — consolidation.
There is plenty of real world data to back this up. When analyzing the findings of Momentum Cyber's 2022 Cybersecurity Almanac, I summarized the likely outcome for companies growing revenue at less than 20% per year:
Any public cybersecurity company in Momentum Cyber's "low growth" category is fair game for an acquisition or takeover.
That's the feast or famine world we're living in right now. When public markets value revenue growth above all else, companies have to deliver and produce growth or get acquired and refactored until they can.
With the recent downturn in public markets, preferences may shift towards profitability and EBITDA over growth. For the purposes of this discussion, what matters is that public or private companies who aren't doing well at whatever investors want — whether that's growth, profitability, or something else — are candidates for consolidation.
When I wrote the Momentum Cyber article in February 2022, these were the numbers for "low growth" companies involved in consolidation discussions:
Three of the 13 remaining companies in the 2021 "low growth" category (excluding Mimecast, NortonLifeLock, and Avast) are already in M&A talks. That's 23% of the low growth companies, consistent with last year's rate. And there's still a lot of time left in 2022.
Since then, Mandiant was acquired by Google, Datto was acquired by Kaseya and SailPoint was acquired by Thoma Bravo. That's a lot of consolidation in a short period of time. At a macro level, the consolidation happened because each of these companies operates in either the "shake out" or "mature" stage of their respective industry lifecycles.
A little over two months have passed since February, but there's still a lot of time left in 2022. If public markets continue to struggle and private equity funds remain well capitalized, we're going to see a lot more consolidation. Public cybersecurity companies will be taken private, and companies in the IPO pipeline will exit to private equity or get consolidated into larger tech companies.
Professional services is another classic example of consolidation within mature industry segments. One of the main observations I discussed about Momentum Cyber's 2022 Cybersecurity Almanac was the high volume of M&A activity within cybersecurity professional services:
Activity is high because mature industries consolidate. Transaction volume is low because services have less leverage than software. Professional services is a mature, low-leverage industry within an otherwise growing and high-leverage cybersecurity ecosystem.
Explained visually, this is where most cybersecurity professional services companies sit on the industry lifecycle:

Cybersecurity professional services almost exactly meets the definition of a mature industry segment: little to no growth, consolidation, and high barriers to entry. It's important to remember this is an average across the entire industry. The characteristics of a mature industry will generally hold at an aggregate level, but there are often one-off outliers.
Exceptions start to happen when you change the scope of the industry segment you're looking at. Narrower (or niche) industry segments for specific types of fast-growing professional services see rapid growth and lower barriers to entry.
I run an independent consulting business and certainly didn't feel the barriers to entry were high, but I'm also not competing against Big Four firms for multi-million dollar enterprise cybersecurity projects. That's where strategy comes in — outcomes depend a lot on how you define and approach opportunities in an industry segment.
Zooming back out to the cybersecurity ecosystem level, professional services is somewhat of a negative outlier compared to other parts of the ecosystem. I described it like this:
The M&A numbers for professional services stand out within the ecosystem because earlier stage sectors don't consolidate as frequently. They're focused on organic growth and making the overall pie bigger. Almost every other sector of the cybersecurity ecosystem is still in the growth stage (or earlier).
It may have been imprecise to say that almost every other sector is in the growth stage, but it's still fair to say that a lot of them are. This macro-level distinction matters when we're applying the industry lifecycle to the entire cybersecurity ecosystem.
On average, the cybersecurity ecosystem is somewhere between the "growth" and "shake out" stages of the industry lifecycle. That explains a lot — why we're seeing lots of investments, new startups, high valuations, and all the other positive things that come along with being on a high growth trajectory.
Jeremiah Grossman had an interesting observation about consolidation that I wanted to briefly address before moving on to the topic of aggregation. Here's the direct quote from Twitter:
Despite what many say, the InfoSec market never goes through “consolidation." It functions more like a hydra. When a company gobbles up a start-up, 2 more pop-up.
— Jeremiah Grossman (@jeremiahg) April 29, 2022
This is interesting because he's right. There are all kinds of examples in cybersecurity — one being the set of authentication companies like Stytch, Hypr, and more that gained momentum (and valuation) after Auth0 was acquired by Okta.
Grossman's observation was somewhat absolute (as Twitter does...) but still directionally accurate. In reality, what happens is more nuanced. Consolidation does happen, but it's quickly followed by an emergent set of companies (essentially a new iteration of an industry segment) that solve a similar problem better — or wants to, in hopes of achieving a similar or better outcome as the company that was acquired.
The important takeaway is that dynamic and growth-oriented ecosystems like cybersecurity make things like this possible. When you're operating in an industry that's early in the overall lifecycle, it's possible to have both good exits and opportunities for new companies to fill the void.
That's a fortunate position to be in — especially compared to, say, starting a printed newspaper in 2022. It's advantageous to be building with macro-level tailwinds than going against the grain in a mature or declining industry.
...But Aggregation Is Happening to Cybersecurity
Consolidation and industry lifecycles are a challenging topic already, but now it's time to really stretch the mind. Aggregation Theory is one of the most powerful concepts in tech and business strategy that relatively few people understand — and even fewer within cybersecurity.
Right now, we're somewhere in the middle of aggregation in cybersecurity. Distribution power is still disaggregated, but many of the ingredients for aggregation exist.
There isn't a pure aggregator in cybersecurity — certainly not in the way of Google, Facebook, Netflix, or any of the tech aggregators that Stratechery talks about. Most cybersecurity companies are subject to this constraint (from Stratechery):
Any business that creates its customer value in-house is not an aggregator because eventually its customer acquisition costs will limit its growth potential.
Cybersecurity companies create their customer value in-house. They build products or offer services that are sold to customers (usually businesses). In most cases, there aren't two sets of parties to aggregate. It's a direct supplier to customer relationship. Some companies have a fair amount of control over the customer relationship — particularly those with bottoms-up adoption models — but there isn't serious modularization of suppliers.
For example, cybersecurity professional services companies sell services primarily based on relationships. A buyer at a company wants to hire consultants for a project, so they send out an RFP to a few firms or call someone they know who works at one.
Large cybersecurity consulting firms are powerful in the legacy distribution-based model because they own high-level customer relationships. Having relationships and the scale to navigate enterprise procurement processes is a challenging distribution problem to solve. Controlling this part of the distribution allows firms to sell an outsized amount of services.
In this legacy model, creating a service offering isn't the hard part — it's owning the distribution channel to sell the services that's valuable:

Aggregation Theory turns models like this upside down. When aggregators enter the picture, legacy distribution models get reformed. Aggregators own the customer relationship and commoditize suppliers:

For example, AWS is aggregating professional services within its marketplace. If an AWS customer wants to hire a Managed Security Service Provider (MSSP), they can browse a list of AWS Managed Security Service Providers and hire one directly from the marketplace — no relationships, procurement processes, or contract negotiations required.
HackerOne is another good example of aggregation at a (currently) smaller scale. The platform aggregates demand for application security and pentesting services from businesses with supply from independent security researchers and ethical hackers. HackerOne modularized suppliers and aggregated demand for pentesting services — a classic example of aggregation.
More importantly, macro-level aggregation happening outside of the cybersecurity ecosystem will have a significant impact on multiple parts of the ecosystem. Aggregation is happing at the infrastructure layer (cloud computing, a layer above cybersecurity). Aggregators like AWS, Google Cloud, etc. are modularizing suppliers and owning relationships with customers (companies of all sizes, in this case — not consumers directly, as with many of the traditional Aggregation Theory examples).
The impact is that cloud providers are starting to modularize cybersecurity companies. In recent earnings discussions, companies like CrowdStrike, CyberArk, and SailPoint, have all talked (optimistically) about their marketplace growth and ramping up sales efforts to grow this channel.
That's fine, however, it's important to recognize what's happening here. Cybersecurity companies aren't the ones doing the aggregating; they are being aggregated. Aggregators (cloud providers) are modularizing suppliers (cybersecurity product companies) and using control of customer demand (businesses using their cloud services) to control distribution of products and services (via marketplaces).
Sometimes, these redefined relationships cross a certain threshold of success or strategic fit, and the cloud provider just builds or acquires a company. This is partially what happened with Mandiant and why it made sense for Google Cloud to acquire them. This trend is likely to continue whenever an aggregator recognizes that integration of a supplier is more valuable than commoditization.
What to Expect in the Future
Concepts like the industry lifecycle, consolidation, and Aggregation Theory aren't going to tell us specifically what will happen in the future, but they do provide a useful framework for what's going to happen.
For me, that's actually comforting. Understanding business strategy concepts like these de-mystifies major events that happen in the cybersecurity ecosystem. Instead of feeling like we're part of a bizarre and twisted game, we can understand the rules and start to play within them.
Metaphorically, think of these concepts like a children's coloring book. We know what the shape is going to look like — the book gives us the outline. It's up to the child to choose the exact colors and design that happen within the coloring book (or whether they stay inside or outside of the lines!).
That's what these concepts do for business strategy. They give us the outline and tell us what the industry is eventually going to look like. Similar to the child creating the art, it's up to us (participants within the industry) to determine exactly what's going to happen within the lines.