Y Combinator hosted its Winter 2022 Demo Day last week from March 29-20. This batch included the largest number of cybersecurity, privacy, and trust companies in the history of Y Combinator.
Twelve companies within these domains were among the 393 companies in the W22 batch:
-
Agency: Managed security and privacy for individuals and growing companies.
-
Bunkyr: Account recovery without seed phrases or backup codes.
-
Cinder: Operating system for trust and safety.
-
Firezone: Open-source alternative to corporate VPNs.
-
JumpWire: Data security for every API and database.
-
Netmaker: Automated WireGuard networks for distributed systems and Kubernetes.
-
Palitronica: Solutions to defend critical infrastructure and key resources.
-
Reality Defender: Enterprise deepfake detection.
-
Rownd: Instant user accounts and authentication.
-
Sarus: Protect access to personal data for analytics or machine learning.
-
Strac: Safely exchange sensitive data with customers and partners.
-
Vista: Enable role-based access across customer groups.
This article takes a deeper look at all 12 companies, their opportunities, and their challenges going forward. Twelve companies is a lot for one batch — nearly twice as many as the seven companies I covered in the S21 batch (a nostalgic article, too — the first one I ever wrote on this site).
Unsurprisingly, this is a long article. Each company is a standalone section, so feel free to skip around or read about the ones you're most interested in. There is some cross-referencing between similar companies, but the commentary about each company generally makes sense on its own.
Now, on to the companies.
Agency
What does the company do?
Agency's is best explained in the company's own words:
"Agency performs enterprise-level cybersecurity for individuals at the highest risk of cyberattacks because of their job, employer, or industry."
In tangible terms, they provide a managed bundle of products and services for cybersecurity and privacy. For security-focused people like us, the bundle is excellent: antivirus/EDR, password manager, dark web monitoring, personal information removal, cyber insurance, and security monitoring services.
Agency provides many of the services that companies get from Managed Detection and Response (MDR) and Managed Security Services Provider (MSSP) services, but for individuals and growing companies.
Where do they fit into the cybersecurity ecosystem?
Agency is bundling multiple parts of the cybersecurity ecosystem. They provide a productized service for individuals and smaller companies. Their offering maps to:
The unique twist is that these area of the cybersecurity ecosystem are historically enterprise-grade products and services. Making them accessible to individuals and small companies is incredibly appealing. I expect they'll continue adding more products and services to the bundle over time to make the value even more compelling than it already is.
What are their challenges?
Inertia is likely the biggest challenge Agency faces today. Average consumers either don't know they should have a bundle like Agency, or they aren't willing to pay $20+/month ($240+ annually) for it.
People earlier on the adoption curve (people like you, if you're reading this) understand the importance of security at both an individual and company level — and have the means to pay for it. As we learned when exploring 1Password's adoption curve, the consumer and B2B market of early adopters (enthusiasts and visionairies) is more than enough to build a large company.
Preferences and switching costs are also a potential challenge. Some people already have parts of the bundle and may not want to give up the services they're already using. Agency has a growing list of partnerships, though (1Password is included as part of the subscription, for example). I don't see this duplication of services as a major challenge. The value of the bundle is still incredible, even with some duplication.
Finally — and perhaps more of an opportunity than a challenge — Agency needs to crack the code on enterprise sales and get companies to provide Agency to employees as a perk. We already know enterprises can be a great channel (Calm for Business, as one example). Companies buying Agency for employees is a clear win-win: a great perk to provide, and a nice growth channel for Agency.
Why could this be a big company?
Agency is a useful solution to a tough problem in a sneaky large market. The "individuals at the highest risk of cyberattacks" part of their company description is a lot bigger than you might think.
In the past year alone, we've had journalists targeted by nation-states, a billionaire hacking experiment, and more. I would definitely put people like you and me in that classification as well.
Agency is one of my favorite companies from this batch. I backed that statement up with my money — I like this company so much that I bought a plan for myself. You should, too (they're not paying me to say that).
Getting all these services for $20 month (with an individual plan) feels like I'm getting far more value than I'm paying for. It's a "how do they give me all of this profitably?" type of reaction, in the best possible way. I have wanted a service like this for a long time, and I'm excited it's finally here.
Strategically, what they're doing is right in line with my previous thoughts on bundling and blue ocean strategies. They're building a new type of business model and using scale to provide differentiated value to a new-ish type of customer. As we've seen with 1Password and a handful of other companies in cybersecurity, that's a recipe for success.
Bunkyr
What does the company do?
Bunkyr is a full-blown account recovery platform delivered to developers through an API. For security-focused products, the traditional approach is to issue recovery keys when accounts get created. Users are responsible for storing them...somewhere.
Bunkyr addresses the nebulous somewhere issue by providing a white-label service developers can integrate into their apps. It gives users an account recovery workflow to securely recover their accounts (and data, more importantly) without the need to store recovery keys or follow any less secure processes.
Where do they fit into the cybersecurity ecosystem?
I would broadly map Bunkyr into a combination of Access Control and Encryption. They're creating a new category by breaking off a specific (and gnarly) piece of authentication and authorization.
What are their challenges?
As the saying goes, old habits die hard. Making developers aware a solution like Bunkyr exists and convincing them to use it instead of plain ol' recovery tokens is a challenge the company will have to solve.
Some products (and the developers who build them) don't value account recovery highly enough to seek out an advanced solution like Bunkyr. We're still teaching developers not to roll their own auth:
Shout it from the rooftops.
— Dan Moore (@mooreds) October 14, 2021
Would you build a database for your app?
If not, why are you building auth for your app? https://t.co/7HC5rmJBG4
...let alone not building a seemingly obscure feature like account recovery tokens and workflows.
That said, there are likely enough (and increasingly more) companies and products who do care about account recovery — the new generation of user-friendly cryptocurrency wallets, for example. No company was going to solve this problem on their own, but there are plenty who would be happy to use Bunkyr as a simple API integration once they know about the product.
Why could this be a big company?
Account recovery might seem like an obscure problem until you realize that 20% of minted Bitcoin — roughly $172 billion (!!!) at today's BTC price — has been lost forever, largely due to this exact problem. And Bitcoin is just one of many instances of the problem.
Companies could build their own account recovery solutions, as they have in the past with account recovery keys. But there's no point. Just plug into Bunkyr's API, and the problem is solved.
Advanced security is becoming both an important feature and a central part of the value proposition for an entire class of new products. Bunkyr could be the right solution at the right time for this problem domain.
Cinder
What does the company do?
Cinder is a platform that powers trust and safety teams — typically companies with social products or user-generated content. It's a purpose-built set of workflows that helps these teams manage reviews and decisions for abusive content, fraud, and threats in their platforms.
Where do they fit into the cybersecurity ecosystem?
Cinder is interesting because it's purely a trust and safety platform, not a cybersecurity platform. I'm broadening the traditional definition of cybersecurity and privacy to include trust and safety as a topic within the ecosystem; however, it's a different set of users and buyers within a company.
My original cybersecurity ecosystem mapping didn't include trust and safety, content moderation, censorship, or any related topics. In hindsight, this feels like an omission. I'm planning to fix it in the next version.
What are their challenges?
Finding customers at the right level of traction and scale to require more advanced trust and safety operations is potentially tricky. Small companies with seed funding or earlier are usually still seeking traction. This doesn't leave much room to focus on problems outside of growth — trust and safety being one such problem.
There is also a lot of variety in this space. Trust and safety threats and problems vary by company and by industry, as do the processes for solving them. Cinder offers customizable workflows for this exact reason, but managing the variety is a potentially difficult product management challenge.
Why could this be a big company?
Problems with abusive content, fraud, and threats were a nascent problem that only existed in the world of large social media companies. Or so we thought. We've now entered an era of misinformation, abuse, and outright information warfare that causes massive societal problems and elevates the discussion about trust and safety into the public spotlight.
Large social media companies like Facebook (where Cinder's founders came from) and Twitter already have dedicated trust and safety teams. The problems in this domain are far from solved, but these companies are leading the way forward. For companies who aren't at the scale of Facebook or Twitter yet, the problems of trust and safety remain somewhat nascent and unaddressed.
When writing about my observations from mapping the cybersecurity ecosystem, I wrote that problems in trust and safety (I referred to them as privacy, censorship, and content moderation) need to be solved by qualified people from large tech companies:
Unfortunately, some of the most pressing problems in privacy, censorship, and content moderation can only be solved by large tech companies like Facebook and Twitter. They have large, specialized teams of their own and don't need to spend much time looking externally for solutions, even if they should.
A potential exception is qualified people from large tech companies (with an understanding of the problems they face) who leave and build a company. Without good regulation to guide the market, the people with the best chance of creating a positive impact are likely the ones who understand the problems and nuances from the inside.
That's exactly what happened with the co-founders of Cinder. Qualified people from Facebook's trust and safety team left to build a company. They understand the problems and nuances from the inside, which means they can productize and help teach everyone else the leading practices for trust and safety. This gives Cinder a huge advantage in winning this market.
Firezone
What does the company do?
Firezone is an open source Virtual Private Network (VPN) server and firewall. It's built on Wireguard, a shiny new VPN protocol that's faster and more secure than the old school ones your company is probably using today (especially if you work in an enterprise).
Where do they fit into the cybersecurity ecosystem?
Firezone fits quite nicely into the Virtual Private Networks (VPN) segment of the cybersecurity ecosystem.
One slight nuance is that Fireguard is meant for teams and includes lots of business-focused features. This differs from consumer-focused VPNs like NordVPN or ProtonVPN. The concept of a VPN is the same for both consumers and businesses, but the products and management features differ depending on the type of customer.
What are their challenges?
The market for VPNs is mature and crowded. In the internet era, VPNs are as old as time. There are a lot of companies who make VPN software (over 200, according to a quick search on company data). In crowded markets, standing out from competitors is hard.
Inertia could play a factor in their success. Most businesses already have VPNs, and some are going to be content with "good enough" speed and security — or barely consider it at all. In cases like this, getting companies to switch usually requires an exponentially better product or another significant differentiator to break the inertia.
There is a (surprising?) amount of innovation in network architecture. Emerging paradigms like, Zero Trust, Secure Access Service Edge (SASE), and software-defined perimeter (SDP) aim to replace VPNs with more granular levels of control. These trends are still being sorted out, and companies are early in the adoption cycle. However, if the trends catch on, the role of VPNs could be diminished.
Finally, WireGuard is an open source protocol. That means anyone can build a VPN product on top of it, as many companies have. Plenty of companies have done well at building from open source software (YC's own GitLab is one great example), so it can definitely be done — it's just an additional challenge to overcome.
Why could this be a big company?
The COVID-19 pandemic essentially made every company a remote company. If companies didn't have a VPN before March 2020, or if their existing VPN was too slow, insecure, or scaled poorly, they were in trouble.
Two years later, it's clear that remote and hybrid work are going to stick around in some shape or form, even as the pandemic subsides. This mega-trend elevates the priority of VPNs significantly — they're basically mission critical now.
If Firezone can build an awesome product with blazing fast speed and exceptional security, companies will adopt it. As a startup, they can also move fast and expand their products to address emerging network architecture trends and become the de facto open source company for everything related to network access.
JumpWire
What does the company do?
JumpWire protects sensitive data in applications and APIs. The product proxies requests from users and applications to dynamically (and virtually) encrypt sensitive data fields. This overview diagram is super helpful:
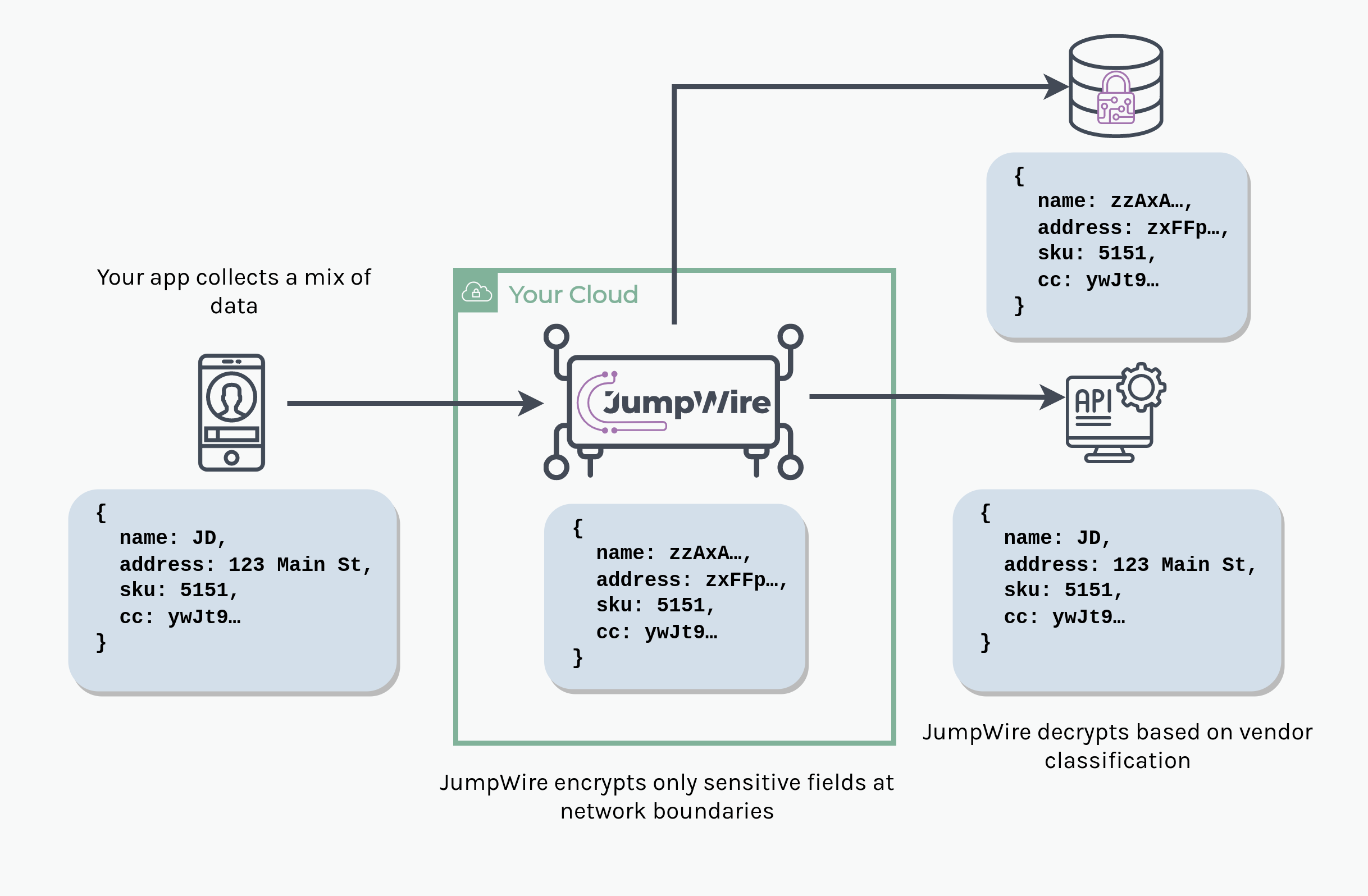
Instead of using database-level encryption to encrypt specific fields (or entire tables or databases) in a database, JumpWire does the encryption on the fly. It also helps customers find their sensitive data in the first place.
Where do they fit into the cybersecurity ecosystem?
I would generally classify JumpWire into Database Security and API Security. The product is also similar to a few products within the Privacy By Design category, which includes data anonymization and developer-focused privacy tools.
What are their challenges?
Adoption, by far. Changing developer behavior is hard. In Observations About the Cybersecurity Ecosystem in 2021, I said this about developer adoption for privacy-focused developer tools:
Privacy-focused developer tools and the concept of Privacy By Design have a better chance of adoption in the near-term. As discussed earlier, DevSecOps is gaining traction quickly. Privacy-focused dev tools are very closely related and are already making their way into the workflows of forward thinking dev teams.
There are lots of emerging solutions in this space, so it's a race to become the de facto approach and tool for solving the problem of data security.
There are also a couple technical challenges that customers will ask about (I'm sure they have already thought of these):
-
Performance: JumpWire proxies database and API requests, so how does the proxying and on-the-fly data classification and encryption impact performance?
-
Availability: How do we keep our [insert application or service accessing data through JumpWire] available if JumpWire goes down? What is the operational impact?
-
Security architecture: What controls need to be in place to prevent users or applications from connecting directly to the database/API and bypassing the JumpWire proxy?
All of the technical challenges are minor — they're implementation details that are easily overcome. Adoption is a tricker problem to solve.
Why could this be a big company?
JumpWire is a nice solution for a converging set of problems and opportunities. Data loss/leakage is a serious problem, as demonstrated by many recent data breaches. Privacy regulations add a layer of obligation and concequence on top of this. Security-minded developers are also becoming more aware of the need to protect the data their applications consume.
There definitely isn't a "one best way" to implement field-level data security yet. Products like Skyflow take the approach of securing your data in their own vault and exposing it via API. JumpWire essentially takes the opposite approach and inserts the product in front of any API or database you want to use.
JumpWire could become the go-to option if they gain favor with developers and build a product that makes it easy and fast for them to do the right thing with their sensitive data.
Netmaker
What does the company do?
Netmaker is an open source virtual networking platform for building networks between distributed systems. It's built on Wireguard, which makes the connection speed faster than other secure networking protocols.
The company gives a helpful mental model to describe what they do: "Think of Netmaker like your VPC for distributed systems."
If Netmaker sounds familiar to Firezone, you're right on track. Netmaker and Firezone are both VPNs built on the Wireguard protocol. The difference is that Netmaker is focused on building secure virtual connections between cloud networks and workloads, while Firezone is focused on business users and endpoints.
Where do they fit into the cybersecurity ecosystem?
Netmaker could technically be classified as a Virtual Private Networks (VPN); however, it's more accurate to map the company under Secure Networking.
What are their challenges?
Similar to Firezone, there are a lot of product and protocol options for businesses to set up secure network connections. A lot of them are slow, hard to configure, and generally a pain — but they eventually work.
Netmaker needs to gain traction with infrastructure engineers, SREs, and similar people who care deeply about the nuanced problems of network engineering and security. The GitHub repo for their open source project has 3.5k starts — clearly evidence of initial traction with their users.
Why could this be a big company?
Netmaker's real value is simplifying multi-cloud network connections and making them more performant. Early stage companies are usually able to keep their infrastructure within a single cloud, but growing startups and enterprises quickly run into this set of multi-cloud problems. It's a larger market than you might think.
Unlike consumer VPNs, the rise of remote work isn't a driver here. However, continued (and exponential) adoption of cloud computing is. Netmaker will be successful if it becomes the de facto option for building secure network connections in distributed cloud systems.
Palitronica
What does the company do?
Palitronica builds products that protect criticial infrastructure (Operational Technology, or OT) and hardware supply chain components from cybersecurity attacks.
The company currently makes two products, Palisade and Anvil, that protect devices at runtime and provide hardware assurance over manufactured devices and semiconductors.
OT security came into focus in 2021 with the high profile Colonial Pipeline ransomware attack. Hardware security has been, and continues to be, a glaring area of concern for many companies and nation-states. Palitronica is stepping in to help protect these important physical assets.
Where do they fit into the cybersecurity ecosystem?
Palitronica is part of the Physical Security domain of cybersecurity. Their current products map closely to Operational Technology (OT) Security.
What are their challenges?
Hardware security is an advanced domain within cybersecurity, which can unfortunately make products like Palitronica hard to understand for many cybersecurity professionals. Awareness is definitely a challenge, but it only matters that the people who are truly buyers understand what the product does and the value it brings.
Many of Palitronica's early customers are government agencies, which are notoriously slow moving and technology averse. Long sales cycles and slow adoption are an inherent challenge of working with the public sector. However, they've already demonstrated several nice wins for an early stage company.
Why could this be a big company?
Palitronica feels like it has a Palantir-esque mystique — a company with advanced technology solving an important societal problem. Even if hardware security isn't well understood by most people in the world, it's still a serious problem that has a high probability of getting worse.
The company is founded by domain experts with decades of experience in academic research around embedded systems at the University of Waterloo. It's a competent team who understands how to solve the difficult problems the industry faces.
Palitronica is the type of company that can be more than just big if their product truly is a significant advancement that gains adoption by governments and device manufacturers.
Reality Defender
What does the company do?
Reality Defender is a platform that helps companies, governments, and journalists detect fake media content (aka deepfakes). The company originated as a project incubated by Microsoft and the AI Foundation. It's now a standalone company with products that make deepfake scanning available via a web interface and API.
Where do they fit into the cybersecurity ecosystem?
Deepfake detection is an emerging subcategory within Artificial Intelligence that I didn't include in my original cybersecurity ecosystem mapping. This should be included in a future version as companies are now starting to emerge with products to help address the problem.
What are their challenges?
People are skeptical, if not outright terrified, of deepfake detection technologies because of how their models are trained (and numerous other ethical issues around AI in general). The discussion around Reality Defender's Hacker News launch was long, spirited, and sometimes unpleasant.
The HN community raised several good points that are challenges Reality Defender will need to overcome:
-
Deepfake detection can theoretically improve the quality of deepfakes if bad actors treat it like a game.
-
Retrospective, pattern-based techniques for deepfake detection are inherently always behind the latest and greatest deepfake generation techniques. It's a cat-and-mouse game.
-
AI models used for deepfake detection are only as good as the datasets used to train them. Unfortunately, many of those datasets contain inadvertent (or explicit) bias — especially towards gender and ethnicity — which subsequently bias the results of the model.
-
Even if the tech works reliably, users can still misuse it if their intentions are questionable.
These challenges (and more) are all very real, but combatting deepfakes is also an important problem. Reality Defender feels like a team who can make significant advancements towards addressing them.
Why could this be a big company?
The problems created by deepfakes — and fake content in general — are getting exponentially worse (in volume) and more complex to combat. It's hard to overstate the potential magnitude of this set of challenges.
The Reality Defender team drew an interesting parallel in their Launch HN overview that made the importance of their solution click for me:
As with computer viruses, deepfakes will continue evolving to circumvent current security measures. New deepfake detection techniques must be as iterative as the generation methods.
Put differently (my words, not theirs), deepfakes are like viruses for the human mind. Psychological operations are bad — basically at a level of bad that can disrupt the stability of entire nation-states and international relations. We need the best possible tech humankind can invent to counter these types of attacks.
On a more down-to-earth and practical basis, deepfakes are behind a lot of the fraud that occurs within the financial system. Unsurprisingly, many of Reality Defender's early customers are financial institutions.
Reality Defender is in a good position because they have very tangible, quantifiable, and important problems that can be addressed right away (things like fraud) while they continue to make progress towards massive global issues like psyops and information warfare.
Rownd
What does the company do?
Rownd helps companies onboard new users faster and keep them authenticated across multiple sites. It replaces an application's back end user store or third party authentication platforms like Auth0.
Developers can use the product by embedding a code snippet, then decide how deep they want to take the integration from there. The product is mostly white-label and ranges from a visible component for sign-in to full integration with your own form code.
In more technical terms, Rownd proactively onboards users by creating anonymous accounts for any visitor to your site. They create an "unclaimed" account for the user and enrich it with additional information, if available (e.g. from a newsletter, CRM, or other service).
Once the user decides to register, they simply claim the account that was already there for them and use it for continued authentication and authorization as they use the product. Think of it like proactive onboarding.
Where do they fit into the cybersecurity ecosystem?
Rownd is technically an authentication product; however, that classification is nuanced. TL;DR: it's more of an onboarding product that happens to do authentication.
I thought Rownd's CEO, Robert Thelen, did a nice job of explaining this nuance in one of his replies to the Hacker News discussion:
We create accounts that span apps and websites - and we happen protect them.
We want to kill the login page. We want first time users to be able to enjoy an app or website first and then, when they fall in love with the product, then you ask for validation/authentication.
Authentication is more of a check box for us, what you do with the data is our product.
What are their challenges?
Rownd's current challenge seems to be helping potential users quickly understand what the product does and why it's valuable. One of the main themes of the discussion from their Hacker News launch was people trying to figure out those exact questions.
I'm a good case study: I know a lot about identity and access management (and have written about it several times here), and it still took me ~15 minutes to finally understand what Rownd is doing and how it works. Most potential customers aren't going to spare them that much time.
Part of this challenge (and opportunity, perhaps) is that static login pages are such an entrenched paradigm of internet use that they're part of everyone's mental model about onboarding. Killing the static login page breaks this mental model, and people are left wondering what would replace it.
Belaboring this point is being nit-picky — Rownd will figure out its marketing. They already made several updates quickly based on HN feedback, so props to them for learning and moving fast. This probably isn't a long term challenge.
Bigger picture, the authentication market is brutally competitive, as I've said many times before. There are well-established companies that are already public, a set of late-stage startups ready to IPO, and another set of well-funded early stage startups. This competition is great for customers because it creates innovation, but it's hard for individual companies who may or may not win the market.
Why could this be a big company?
The path to becoming a large company in this market is somewhat established already. Auth0 did it, and companies like Transmit Security aren't far behind. No company's path is ever the same, but we have an idea about what it takes to be successful here.
Rownd's growth trajectory and TAM is similar to other high growth passwordless authentication companies — they need to gain developer adoption, attract other high growth companies as customers, and increase volume together as their customers grow.
The idea of proactive onboarding is fairly revolutionary. It's a "why didn't anyone think of this before?" type of an idea. Progressive profiling is already an emerging trend in onboarding, and Rownd takes this idea a step further.
If Rownd can gain the favor of developers — and more importantly — the users of their products, they can become a big company. Killing the login page is a lofty but worthy goal to tackle.
Sarus
What does the company do?
Sarus lets data scientists access work with sensitive data in a private way. The product proxies queries from users to dynamically (and virtually) return private results (or synthetic data samples of small datasets) without requiring the end user to see or access the private data.
If this description sounds a lot like JumpWire, you're right. Sarus and JumpWire are conceptually similar but serve different use cases. JumpWire encrypts sensitive data that's accessed by applications. Sarus keeps sensitive data private (using a fancy technique called differential privacy) while still returning large, aggregated result sets for data scientists.
Functionally, the products are similar, but Sarus has a much more specific use case. I wouldn't even call them competitors.
Where do they fit into the cybersecurity ecosystem?
Similar to JumpWire, I would broadly classify Sarus into Database Security. The product also maps to the Privacy By Design category, which includes data anonymization and developer-focused privacy tools.
What are their challenges?
Based on the discussion around their Hacker News launch, people definitely had questions, but the questions were mostly well-intentioned.
There was some feedback about clarifying how the product works, which isn't surprising. This is a different situation than Rownd — Sarus is solving an uncommon problem in a very different way. People seem interested in giving them the time to explain why and how.
The good and bad part about the users and problem Sarus is addressing is that it's specific (or niche, perhaps). You could take that negatively and say it limits their growth potential. However, in the case of an early stage startup, I see it as a good thing. Sarus seems to know exactly what the product does and who it's for.
Why could this be a big company?
Data privacy for data scientists may seem like a relatively niche market, but it's not. Nearly every high growth startup, enterprise, academic institution, and government agency now stores and analyzes petabytes of sensitive data.
Allowing data scientists to do their work while simultaneously keeping data secure is actually an interesting predicament. The Sarus founders described it like this in their Hacker News launch:
It’s a rightful objective to protect data but it should not have to hamstring all innovation. For most data science or analytics objectives, the analyst has no interest in the information of a given individual. They look for patterns that are valid across the dataset. Access to user-level information is just an unfortunate way to get there.
"Access to user-level information is just an unfortunate way to get there" is a great line. Prose aside, it's an insightful example of why Sarus can potentially be one of the first big engineering-focused privacy tools.
In adjacent use cases, engineers actually need to access the data but can't, so privacy is a pain. In the case of Sarus, data scientists don't even need or want to access the data — there just wasn't a way to let them do their work otherwise. Until now. That's why Sarus can be huge.
Strac
What does the company do?
Strac detects and masks sensitive data exchanged by your company and third party services. In today's integration-first SaaS world, this type of data exchange actually happens a lot. Bad things happen when your sensitive data is all over the place — and especially in random third party services where you might not expect it to be.
A particularly acute example was the [24]7.ai data breach that affected multiple Fortune 100 companies. [24]7.ai is a customer support chat service that ended up collecting PII and credit card data from customers to resolve support issues. They got breached, and it created a super messy situation for their large customers.
Where do they fit into the cybersecurity ecosystem?
The closest mapping in my existing cybersecurity ecosystem mapping is Data Loss/Leakage Prevention, but this feels inaccurate. Strac is like a secure file transfer system built for modern, API-based data exchanges instead of old-school file transfers.
What are their challenges?
Strac's near-term challenge seems to be product focus. This could just be my intuition, but it looks like the product is going in a few different directions.
The core set of features are around securely exchanging data with third party services. There is also a data redaction API — which is also helpful, but feels like an adjacent product.
This is the nature of startups. The product will get figured out when specific use cases clearly start gaining traction.
Longer term, the challenge is awareness. Companies integrate third party applications quickly and without consideration for security. An additional security layer like Strac increases friction in an otherwise simple integration process. The value of inserting Strac into the mix needs to be clear, especially for security engineering teams.
Why could this be a big company?
Protecting data exchanged with third party services is a huge win. It's not realistic to expect business teams to avoid third party integrations at all costs. The next best thing is to let them get the value they need without unnecessarily exchanging sensitive data.
Integrations with third party services are growing exponentially to the point of being a mega-trend. Companies like Zapier (a YC company, incidentally) are entirely built around the idea of simplifying integrations between third party services. This trend is definitely not going away, so let's make it secure.
That's exactly where Strac comes in. If they can become the go-to solution for enabling secure integrations between services, they're going to be a big company.
Vista
What does the company do?
Vista is a platform for centrally managing authorization for your applications. Instead of building custom authorization (roles, permissions, etc.), just integrate Vista, and they'll take care of it for you.
The core of the platform is an API. It also includes React components and other handy tools to make integration and implementation easier.
Where do they fit into the cybersecurity ecosystem?
Vista fits into the Authorization category, although I didn't create a specific sub-category for external authorization platforms in the first version ecosystem mapping.
What are their challenges?
Like other developer-focused tools in this YC batch and beyond, the main driver of growth is gaining developer adoption. Vista is squarely in the mold of a developer-first, bottom-up adoption product. They have to win over developers to be successful.
From a developer's perspective, there are risks in partnering with a startup — and especially for something as core as authorization. If you've built authorization in your app using any third party service and the company shuts down, you're in trouble.
External authorization carries a different level of risk than security products that aren't as deeply embedded into a product. The opposite is also a benefit for Vista, though: if customers choose to use Vista for authorization, stickiness and retention is high. Once Vista is integrated and working, there's no reason to switch.
The current wave of companies building external authorization products is also competitive. Sequoia-backed Oso is in this market, and Auth0 released a developer preview of their Fine Grained Authorization product in late 2021. No company has won the market yet, but the competition is heating up.
Why could this be a big company?
There have been many attempts at building an external authorization platform over the past decade, and no company has even come close to winning the market. You could interpret that as a vote against any company in the market; however, the reality is that someone is bound to win it...eventually.
Managing authorization has been a problem developers have faced for as long as applications have existed. Authorization is still a pain to build today. What does get built isn't always great, either — excessive permissions are one of the major contributing factors in data breaches.
A de facto standard for external authorization needs to happen, and now could be the time. Integrating with third party services for non-core product functionality is now widely accepted. Companies have also come to terms with externalizing authentication. Authorization is a much bigger level of commitment, but it's now in the realm of possibility. Whoever wins this market is going to be a big company — probably the next Auth0.
Thanks for reading! How did you like this article?

