What if security was designed for humans and embedded in everything we do? That's the question I took away from Tessian's Human Layer Security Summit last week.
The event was hosted by Tessian, a Series C company founded in 2013. The message was about so much more. We're entering an era of human-centered security. Their products and subsequent discussion at the event give us a look into what the the future of security could hold if design and human augmentation prevail.
Resignation and Bad Vibes
Jess Burn, a Senior Analyst at Forrester, summed up the current mindset of many cybersecurity professionals:
"I was most surprised about the level of resignation that we saw in the data for those security leaders and security pros that have all the traditional email security and DLP tools in place. But none of them are stopping the sophisticated phishing and BEC (Business Email Compromise) attacks.
40% said they see, on average, 10+ employee-related security incidents per month.
It was surprising, but it was also a little bit sad to see that level of resignation because there are solutions out there that can help. It's time to start thinking about what comes next for email security as sophistication only continues to rise."
There is data to back up these bad vibes. Summarizing a few statistics from Forrester's Take Control of Email Security with Human Layer Security Protection study:
-
Employee mistakes cause roughly a third of security incidents in organizations.
-
Organizations experienced between one and 50 employee-related email security incidents per month on average with nearly 40% reporting at least 10 or more incidents per month.
-
61% of security and risk leaders believed that an employee’s actions will cause their organizations’ next data breach.
-
48% of security and risk leaders said human error-caused security incidents will increase in the next year.
In other words: employees cause a lot of security incidents, and most security leaders believe the problem will get worse.
The problems created by regular employees have both anecdotal and measurable impacts on information security teams. I've have previously written about Mandiant CEO Kevin Mandia's observations on the burden placed on these teams:
The combination of increasing threats and a growing shortage of cybersecurity skills means in-house teams are overworked, and they may lack the expertise or visibility to manage their security controls and security posture.
The Forrester report gave us some additional data about one specific instance: email security incidents. Organizations reported spending up to 12 hours of time triaging, investigating, and remediating each individual incident. Total resolution time for all incidents took up to 600 hours per month.
The situation around email security incidents is untenable. It isn't economically viable to be spending 600 hours (or nearly four dedicated FTEs) monthly and still end up with 10 or more qualified incidents per month. We need better results in less time.
It isn't viable from a morale standpoint, either. Most employees don't want to harm their companies intentionally, yet a third of incidents are caused by employees. Information security teams are already strained. Time spent addressing email security incidents could be better focused elsewhere or banked as time not spent to reduce workloads.
Augmented Attackers
On top of the bad vibes and sense of resignation, the news actually gets more terrifying. A research team from Singapore's Government Technology Agency (GovTech Singapore) shared findings about use of AI and data analytics by attackers to increase the quality and scale of their phishing campaigns.
You read that correctly: attackers are augmenting themselves with AI and data.
The simplest use case is generating high quality text for phishing emails. Poor grammar and sentence structure is one of the classic signals rule-based Secure Email Gateway (SEG) products use to identify malicious emails. Content quality can obviously be improved with manual reviews. It becomes exponentially more efficient and scalable with AI augmentation.
This isn't hyperbole. Tools like Copy.ai already exist for marketers. It uses OpenAI's GPT-3 on the back end to generate high quality marketing copy with minimal user input. This exact model can be used for nefarious tools to generate phishing emails. The only thing stopping this reality is AI companies voluntarily restricting use of their APIs. Yep, that's all.
Augmentation scenarios get even more advanced when you start looking at the end-to-end phishing pipeline. According to researcher Eugene Lim, attackers may analyze people at a level of their personality and make this part of their pipeline. They will use AI tools like GPT-3 to generate convincing emails based on personality and likelihood of response.
A highly sophisticated approach like the one Lim described is well beyond simple proofreading of text. When people are being individually targeted with intentionally designed messages tailored to their personality attributes, we're in trouble. There is no current evidence of this exact type of attack in the wild, but the necessary ingredients already exist.
Beyond using AI for quality and accuracy, attackers have started using data to close the feedback loop and iteratively improve the effectiveness of their email campaigns. As Tessian’s CTO Ed Bishop noted in the session:
I can totally see bad actors measuring the click-through rate on their phishing campaigns, and then having the AI learn from what’s worked to feed into the next one.
Does this sound like a marketing campaign? It should — savvy email marketers use a similar approach. I have made comparisons between techniques used by marketing and cybersecurity teams in the past:
Marketing and cybersecurity aren’t as different as you’d think:
— Cole Grolmus (@colegrolmus) October 22, 2021
Marketing tracks activity for profit.
Cybersecurity tracks activity for safety.
Different objectives. Many similar techniques.
This finding from GovTech Singapore takes the connection one step further. Traditional marketing techniques are being used by both the good people and bad people in cybersecurity. With examples like these, it's no wonder information security teams are feeling a sense of resignation.
Designing Security for Humans
Accepting defeat isn't a solution. Relying solely on information security teams (at a micro level) and law enforcement (at a macro level) isn't working. Both are an important part of combating cyber crime. However, we can't leave regular people defenseless. They can't be completely shielded from attacks, no matter how hard we try.
To get ahead of attackers, it's going to take everybody. We need to give regular people more useful tools to help defend themselves and their companies. The path to accomplishing this starts with a mindset shift: we need to design security into people's daily workflows and make it usable.
Karl Knowles, the Global Head of Cyber for HFW, gave the perfect metaphor. Think of your defenses like a football (soccer) team:
-
Strikers aren't great at defending. Email providers are strikers. They stop some malicious content but let lots in.
-
Midfielders are like Secure Email Gateways (SEG). They give you some additional defense and offense.
-
Defenders are tools like Tessian. They back up SEGs and enhance your defense.
-
Goalkeepers are your people. The only way they can keep a clean sheet (allow no goals) is having strength in depth in front of them to prevent direct shots on goal.
We need to build the defenses in front of our goalkeepers. And we need to do everything we can to prepare our goalkeepers for shots on goal. Jess Burn described exactly what to do: "Get to know your humans and how they work."
A good place start is securing communications — exactly what Tessian does. Designing security into people's everyday workflows means giving them clear and informative information they wouldn't have had without technology augmenting them. This gives them the context they need to either take action or not take action based on the circumstances.
Here's a practical example of what a user-facing security design could look like, modeled after Tessian's products:
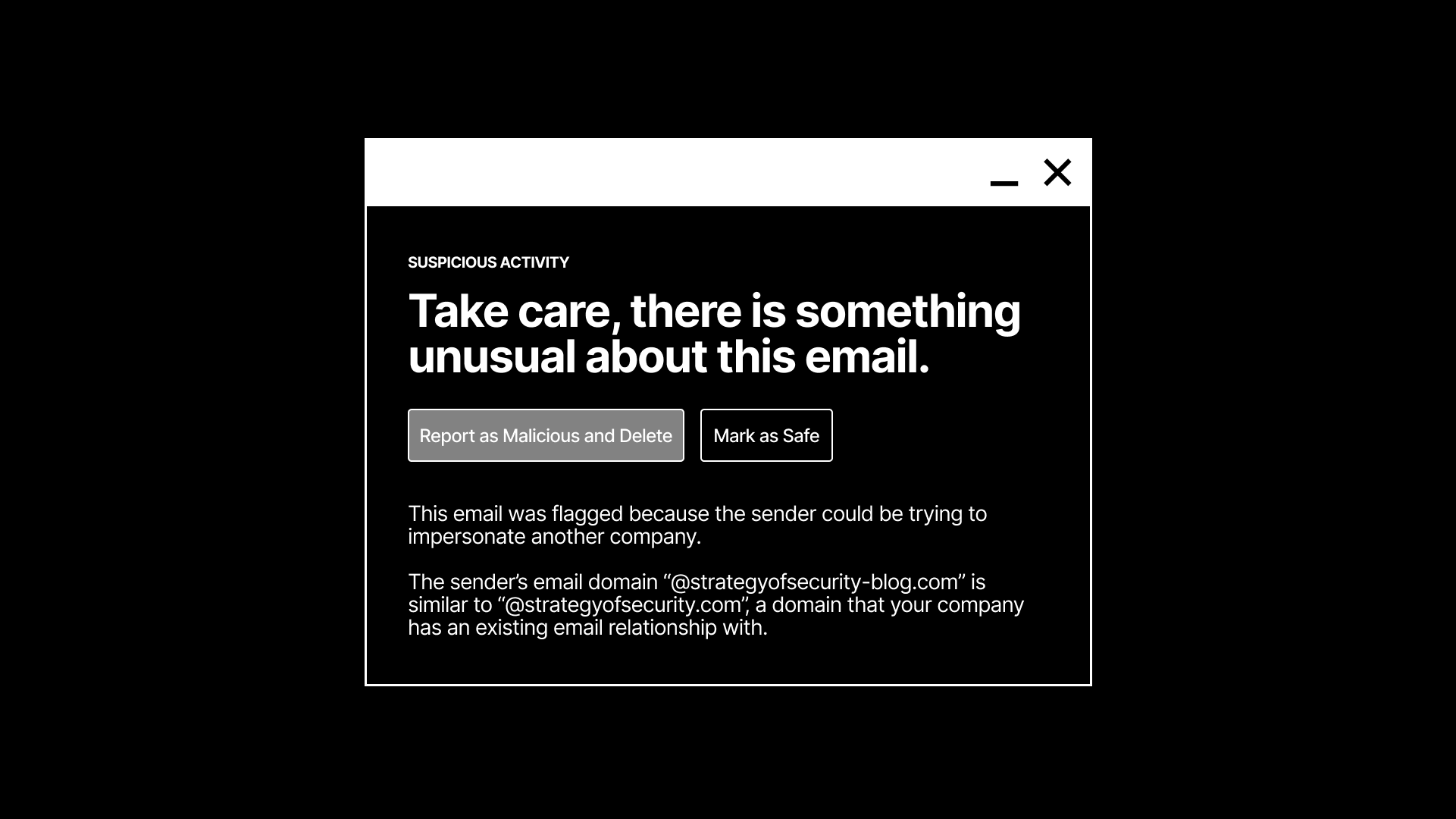
An interface like this is simple and elegant by design. Just because it's simple doesn't mean it's easy. Reaching this level of context is a magnificent feat of engineering and design. At minimum, the platform would need to:
-
Establish a level of trust with the valid domain based on patterns of interaction
-
Recognize the invalid domain doesn't match an existing pattern of interaction
-
Correlate the similarity between the valid and invalid domains
-
Integrate with an email client to enable notifications to be sent to users
-
Design templates for communicating the information in user-friendly terms
-
Prompt the user with a warning when they open the email
-
Record the action the user takes
And that's just a high level overview. Providing human-friendly context in near real-time is one of the most difficult things to do in technology. That's why platforms like Tessian are valuable. Context feels magical when it's implemented well.
Reema Jethwa, a Tessian customer from Schroders Personal Wealth, described the user experience like this:
"I've had users personally comment on the fact that the pop-alerts are really simple to understand and quite user friendly.
They've also said that these prompts happen at exactly the right time, asking them to do the right thing. These pop-ups are there when they need to be told, and it takes seconds for them to do what they need to do.
From a security perspective, we're able to give those extra guardrails to colleagues... We're helping colleagues when they need it, and also not penalizing them... We're building our credibility across the organization."
Exactly the experience we want people to have with security. Experiences like this seem like such a simple and obvious thing to do. In practice, positive user experiences with security happen so rarely that they feel magical when we see them.
Racing With the Machines
We must augment people with well-designed tools and information if we're going to reduce the number and impact of security incidents in a meaningful way. Former Google CEO Eric Schmidt describes the related macro trend as "augmented humanity." From a 2011 speech at the Digital Life Design conference:
“The computer and the human each does something better because the other is helping.”
MIT researchers Erik Brynjolfsson and Andrew McAfee discussed a similar concept in their book Race Against the Machine. Based on research, they observed:
Weak human + machine + better process was superior to a strong computer alone and, more remarkably, superior to a strong human + machine + inferior process.
This observation was true across multiple fields:
This pattern is true not only in chess but throughout the economy. In medicine, law, finance, retailing, manufacturing, and even scientific discovery, the key to winning the race is not to compete against machines but to compete with machines.
Brynjolfsson and McAfee re-framed the traditional, FUD-based mindset that machines are going to take our jobs. This belief is accurate to an extent — some jobs will be automated — but overlooks how technology can be used to improve human performance. The authors call it "racing with the machines" and offer the following strategy for implementation:
How can we implement a “race with machines” strategy? The solution is organizational innovation: co-inventing new organizational structures, processes, and business models that leverage ever-advancing technology and human skills.
In our case, humans can defend against cybersecurity attacks better when computers are helping. I have previously highlighted similar commentary from Kevin Mandia:
I believe automation, powered by AI and machine learning technologies, is the only way organizations will be able to keep up with attacks and maintain resilience. Customers are coming to this realization as well.
Mandia was speaking about using technology to augment information security professionals; however, the central idea is the same: we can't keep up with attacks unless people and technology are working together.
Tessian is a modern example of how this layer of defense gets implemented. Machines analyze communications data, provide people with context when an anomalous situation is detected, and give them tools to resolve the problem without further intervention from an already taxed information security organization. That's how exactly how people and technology can work together to improve security.
While concluding her presentation, Jess Burn put the role of people in practical terms:
"Even though people are a big threat to the security of your organization, they're also the engine of your business. They need to do their jobs, and it's when they try to get around policies or short-circuit those cumbersome security processes that incidents or data loss most often occur.
As these security incidents arise, use those moments and consider providing contextual, in-the-moment coaching which improves their awareness and helps them make the right decisions in real-time.
Make security everyone's responsibility and a daily part of their lives."
Yes, people are responsible for a third of security incidents. Companies are also nothing without them. We need to make security easy to use.
Every job is not going to be automated or replaced with machines in our lifetime. A more pragmatic approach is to double down on any process or technology that makes humans more effective at security. Tessian is leading the way on this movement. It's an exciting journey to watch

